It is always a great notion to know and get acquainted with the basics of something that you want and what it does just like a VPN. With that, before we directly go to the internal functions of a VPN, let us familiarize first its basics.
The abbreviation VPN represents for Virtual Private Network. As the name implicit, it offers consumers with a virtual network, which is personal as a way of connecting themselves to the Internet to a certain extent, which is safe and secure. Fundamentally, the supreme objective of a VPN is to store your data private. With that, there is a corresponding question in that matter, “How does a VPN work?”
great notion to know and get acquainted with the basics of something that you want and what it does just like a VPN. With that, before we directly go to the internal functions of a VPN, let us familiarize first its basics.
The abbreviation VPN represents for Virtual Private Network. As the name implicit, it offers consumers with a virtual network, which is personal as a way of connecting themselves to the Internet to a certain extent, which is safe and secure. Fundamentally, the supreme objective of a VPN is to store your data private. With that, there is a corresponding question in that matter, “How does a VPN work?”
How does a VPN work?
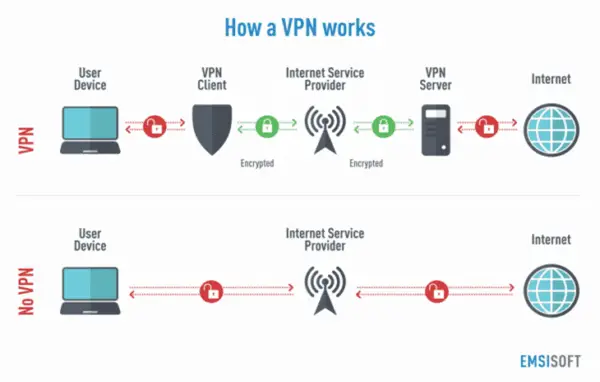
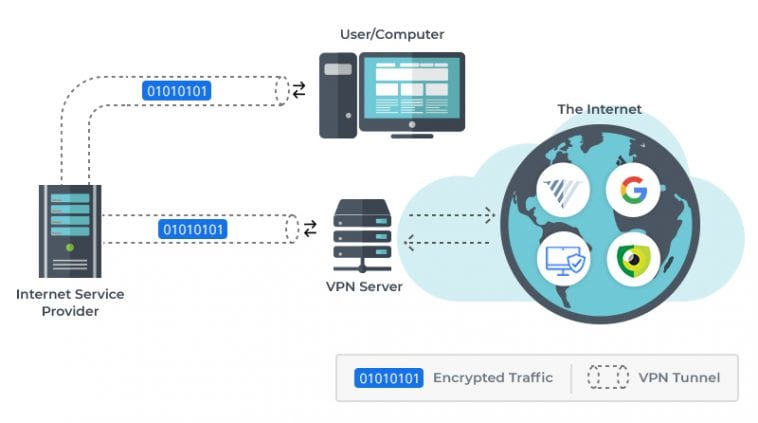
A VPN functions by dispelling the Internet connection from the users’ device through their selected VPN’s server as opposed to their Internet Service Provider (ISP) so that when their information is broadcasted to the Internet, it is from the VPN and not from their devices. A VPN represents as a kind of mediator once they connect to the Internet, by that means, it is obscuring their IP address – a cable of numbers their ISP allocates to their device as well as covers their identity. Moreover, when their information is somehow seized, it will be indecipherable until it arrives at its last destination.
Also, a VPN creates a personal tunnel from the device of its users to the Internet and conceals their important information through encryption.
The fundamentals of encryption
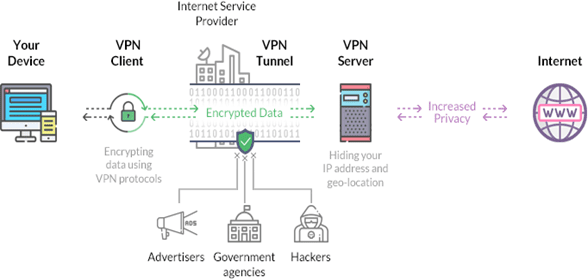
Encryption is the word utilized to narrate how consumers’ information is stored privately when utilizing a VPN. This also secretes data wherein it is unreadable without a vigorous password that is called a key. This key fundamentally splits the intricate code, which their information has been transformed. Only their device and the VPN server have an idea about this key. The procedure of decoding their information is called decryption, which is the procedure of creating encrypted data legible again with the help of the entreaty of the key.
Distinct VPN services utilize distinct types of encryption procedures. However, we can easily say that these procedures go like this:
- If a user connects to a VPN, it is by a shielded tunnel where his/ her information is encoded. With that, his/ her information is turned into an indecipherable code when it goes from his/ her device to the server of the VPN.
- Now, his/ her device is perceived in a similar district network as his/ her VPN. As such, his/ her IP address will also be the IP address of one of his/her VPN supplier’s servers.
- He/ she can peruse the Internet as he/ she pleases, secure in mind that the VPN functions as a barricade that shelters his/ her private data.
However, how successfully users’ information is encrypted relies on the conventions of his/ her VPN supplier’s encryption procedure.
Other things that VPNs do
Though VPNs are equitably easy tools, they can be utilized to do a wide variety of things:
· Ingress a Business Network whilst traveling
Business travelers have an entry in their business’ network that comprises everything in its restricted network assets while traveling utilize VPNs. The restricted assets not necessarily reveal to the Internet, which helps develop safety.
· Access Home Network whilst traveling
Users can still set up their VPN to ingress their networks while traveling. This will permit them to ingress a Windows Remote Desktop through the Internet and utilize restricted file shares like they were in similar LAN.
· Secretes Perusing Activity from Local Network and ISP
Using a public Internet connection can harm the privacy of its users, especially if they browse on non-HTTPS sites, as they can be perceptible to everyone around the area. To hide your perusing activity to have privacy, it is better to connect to a VPN. The restricted network will only perceive one and safety VPN connection while everything in traffic will go onto the VPN connection.
· Access Geo-Blocked Sites

Whether you are an American who is attempting to have an acquisition to your Netflix account, for example, whilst traveling overseas or someone who wish to have access to American websites like Hulu and Pandora, you can gain ingression to these hindered services by connecting to a VPN that is headquartered in the USA.
· Bypass Internet Censorship

A lot of people utilize VPN to go over the Great Firewall like Chinese nationalities, for example. With this, they were able to have ingression to the whole Internet. Nonetheless, the Great Firewall has seemingly begun impeding with VPNs lately.
· File Downloading
A lot of us indeed utilize VPN connections to download files through Bit Torrent, for example. This is helpful even if users are downloading wholly legal torrents – when their ISP is strangulating BitTorrent and creating it highly slow. With that, they can utilize BitTorrent to the VPN to have quick rapidity. This is similar to the other kinds of traffic their ISP might interrupt with even if they do not interrupt with VPN traffic themselves. Several of us have known about VPNs with the help of our employers, who as well understand that the Internet is not that secure. Businesses have formerly utilized them to allow employees remote acquisition to the server of the business. A VPN would provide them acquisition to the software and business expedients while they were outside. As such, they can now simply ingress their home network while having a journey locally or overseas.