Introduction
The guideline to GDPR request is part of the direction to Data Protection. It’s for the DPOs and many others who partake in everyday responsibility for data privacy.
It outlines the overall data privacy management that refers to most UK industries and organizations. It involves the GDPR or General Data Protection Regulation as it relates to the UK, which is designed by the Data Protection Act 2018.
It describes every data privacy rights, philosophies, and responsibilities. It philosophies the significant points you should understand, responds to FAQ, and involves practical efficiency to assist you in fulfilling.
This guideline also connects to more comprehensive supervision and some other resources such as statutory ICO codes of practice, ICO guidance, as well as EDPB or European guidance issued by the European Data Protection Board
Also, you may find other parts of the guidelines to Data Protection informative and beneficial:
- Overview of data privacy – This is about guideline to law and order processing
- Guideline to law and order processing – More about the distinct management for law and order
- Guideline to intelligence services processing – More about distinct management for the intellect services
- Primary data protection matters – For detailed management on significant themes and matters, like children’s data.
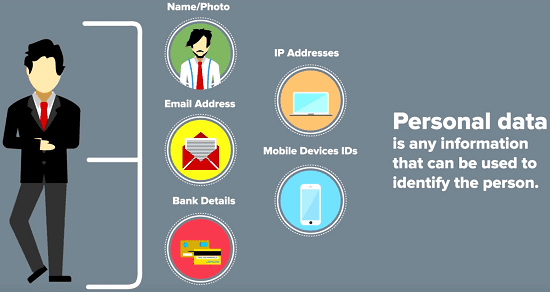
What is Personal Data?
- The GDPR request refers to the handling of private information, that is:
- exclusively or partially by automatic means; or
- The administration but by automated ways of private details which system part of, or projected to system part of, a filing structure.
- Private information only contains info about regular people who:
- Are recognizable or can be known, straight from the data in the request; or
- Who can be implicitly recognized from that data along with any other info.
- Private information also comprises unique groups of private information or illegal sentence and violations files. These are reflected to be a greater sensitivity, and you only handle them for more restricted conditions.
- Pseudonymized information helps lessen security dangers by making it harder to recognize people, but it’s still private information.
- If private information can be genuinely nameless, then the unknown data is not under the GDPR request. It’s crucial to know what private information is in to comprehend if the information has been nameless.
- Data about a departed person doesn’t represent private information, and so isn’t for GDPR.
- Data about corporations or public specialists isn’t private information.
- But data about people working as employees, sole traders, associates, and business directors where they’re separately identifiable and the data links to them as a person may institute private information.

What’s the latest under GDPR Request?
Controllers have the latest data privacy responsibilities under the GDPR request. A change in the former regulation, processors, now takes legal duties in their right as a part of GDPR request.
Individuals and directorial authorities (like ICO) can keep both the processors and controllers held responsible if they can’t fulfill their duties under the GDPR request.
The GDPR comprises precise requirements focused on joint controllers.
What is the right of access?
There are many aspects that you must consider and are written under Article 15 of GDPR. You have all the rights to gain specific information and a copy of that from the data controller. The right to delete, rectify, object, and restrict processing of your data are allowed. When your data is processed, there is extra information such as the purpose, categories, retention period, recipients, and third parties are included.
How to request for access in personal data?
Under Article 15 of GDPR, you have the right to request a copy of your personal data used by controllers in any way. The regulation does not have specific methods in asking for your personal data. You can even do it verbally or in writing. The DPC made an example format for practicality and easier access to the request. It is also essential that you make specifications in what you wish to access in your personal data to ensure that it is not provided in the wrong people.
Will you be collected a fee for requesting access?
In general, making an access request does not require you to pay for a fee. However, there are situations where a controller can collect a reasonable price for the payment in administrative costs to achieve the request. Controllers will be able to grant your request for access, like the way you made the request. If you have particular wishes for a response, they can give it. Making your request using electronic mail, controllers will also provide the information you have requested in the same format, electronically, or otherwise stated.
Are there limitations in access rights?
Under the GDPR, in some cases, if the request is found excessive and manifestly unfounded, the controller can deny the request. This is a complicated one, and controllers must evaluate properly to prove that it is excessive. The cases are few, and the controller usually approves the request when accurately done. This regulation also states that your right to access your personal data should not affect others’ rights. The collector
A collector should balance out the rights of your access and identify the risk earlier it third parties are brought to the disclosure of data. The GDPR stated that the controller must enjoy accepting the request while still protecting all the freedom and rights of others.

Why are principles essential?
The principles remain at the center of the GDPR request. They’re set right at the outset of the law, and update all that adheres. They don’t offer strenuous and quick guidelines, but instead exemplify the essence of the overall information security rule – and so, there are limited exclusions.
Observance with the essence of these major philosophies is, therefore, an essential core element for a good information data routine. Also, it is the key to your practice with specific requirements of the GDPR request.
Unable to conform to the values may put you on extensive penalties. Article 83(5)(a) states that breaches of the fundamental principles for handling private information are under the maximum tier of directorial penalties. This means a sentence of about €20 million, or up to 4% of your total universal annual income, which is higher.
Lawfulness
For handling private information to be legitimate, you must know the exact reasons for the handling, which is referred to as a “lawful basis” for processing, and it is composed of 6 choices depending on your right and connection with the person. Also, there are particular extra conditions for handling especially delicate data types. If you want to know more about the lawful basis, there are more resources available online.
If no legitimate basis refers, then your management will be unauthorized and violation of this code.
Also, lawfulness means that you don nothing with the private information, which is unauthorized in a more overall sense. This comprises everyday law duties and statute, if handling includes committing an unlawful crime, it will certainly be illegal. But also handling may be unlawful if it leads to:
- A violation of responsibility of sureness
- A breach of copyright;
- Your business exceeding its lawful controls or practicing those controls wrongly;
- A failure to meet an executable contractual arrangement
- Human Rights Act 1998 violation
- Industry-specific regulations or legislation violation
These are some of the examples, and this checklist isn’t complete. You may take your lawful information on some other pertinent lawful requirements.
While private handling information breached copyright or business guidelines will comprise unlawful handling in breach of this code, this doesn’t imply that ICO can follow claims, which are mainly about violations of exclusive rights, monetary principles, or many other regulations outside the responsibility and knowledge as information privacy regulator. In such a situation, there are perhaps to be extra-legal or direct ways of compensation where the problems can be measured in a more suitable setting.
If you have handled private information, the GDPR request gives people the privilege to remove that information or limit their handling of it.
Fairness
It should always be fair-minded and legal when processing private data. If a part of your processing becomes partial, you’ll violate this principle, despite presenting an authorized source for the processing.
Fairness is handling private information with people who would rationally assume and unuse it in other methods that have an unjust detrimental impact on them. You stop and deliberate not only about how you use the private information but also if you should
Reviewing if you’re processing data justly depends slightly on the way you get it. If anyone is misled or deceived when the private data is collected, then it’s far-fetched to be right.
To evaluate if you’re processing private information fairly, you take note of more generally how it influences the welfare of the people involved, as an individual and a group. If you get and use the information with most people, it connects unfairly to one person; still, there will be a violation of the principle.
Personal information can, at times, be used in some ways that adversely affect a person without being unfair. What’s important is if such damage is justified.
Veracity and Privacy (Security)
You need to make sure that you have proper security procedures set to protect the private information you keep.
This is the ‘Veracity and Privacy” code of the GDPR request, which is referred to as the security code.
Conclusion
The right of access is not new, and there are few changes that EU GDPR made. As many are becoming aware of these rights, the number of requests they received are increasing. Hence, you must be mindful of the Data Subject Access Request (DSAR) is as an employee of any company and the significance of requesting this.