A Virtual Private Network, commonly referred to as VPN, is a type of programming that enables a safe and encrypted connection. Generally, it is accessed using a less secure network, like that of the public internet. Tunneling solutions and protocols are also set in place in order to encrypt data from the sender’s end, decrypting it at the receiver’s end. Both the address of the sending and receiving networks are also encrypted in order to offer you enhanced security for various online activities.
How VPN Works
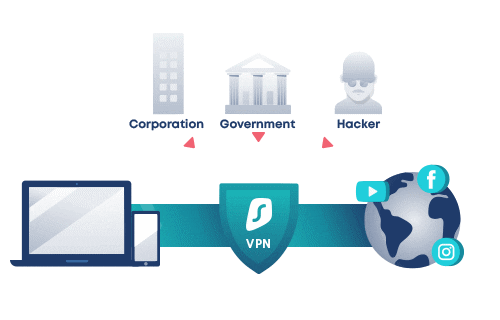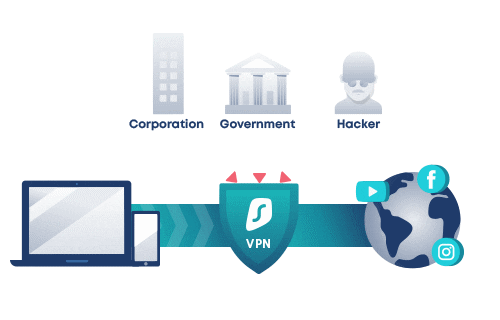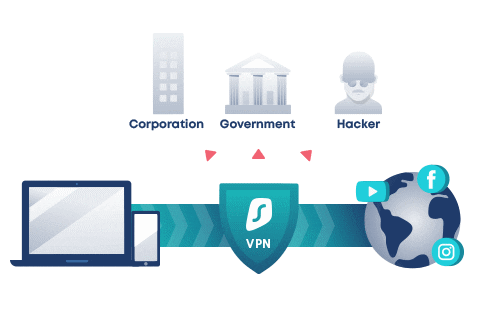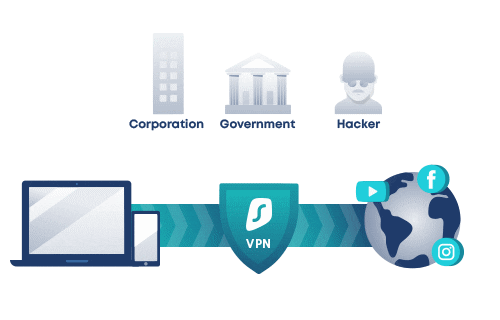
At a very basic level, VPN involves tunneling, which means that it establishes a point-to-point connection that is not accessible to unauthorized users. In order to create this tunnel, the receiving device has to be run on a VPN client either locally or in the cloud. Then, the client should run in the background. To the end-user, this process is not noticeable, unless some performance issues surface.
This performance may also be affected by a number of factors, including the internet connection speed on the user end, the types of protocols implemented by the provider, as well as the specific encryption types used. In a corporation, the overall performance may be influenced by the poor quality of service outside the control of the IT department of an organization.
Different Types of VPNs

There are a number of VPNs that are available these days:
Site-to-Site VPN
A site-to-site VPN utilizes a gateway device in connecting a complete network in a single location to another network of a different location. There is no need for end-node devices in the remote location to have VPN clients since the gateway deals with the connection. Site-to-site VPNs connect through the internet using IPsec. They are also found to utilize carrier MPLS clouds instead of the public internet for their site-to-site VPN transport.
Remote Access VPN
Clients often use remote access VPN connection to a gateway server on the network of an organization. It is the requirement of the gateway to authenticate its identity before being given access to the resources of the internal network. This kind typically depends on either the Secure Sockets Layer (SSL) or the IP Security (IPSec) in order to secure the connection.
Mobile VPN
With this type of configuration, the server is at the company network edge, allowing for a secure tunneled access using authorized, authenticated clients. These tunnels are not connected to actual IP addresses, but they are tied to logical IP addresses. They stick to the mobile device regardless of its location. A dependable mobile VPN offers continuous service to its users, even allowing for a switch across different technologies and networks, both private and public.
Hardware VPN
The use of Hardware VPNs presents different advantages. Aside from offering enhanced security, it also offers load balancing, which is applicable for bigger client loads. The administration is often managed using a web browser interface. As such, a hardware VPN is often more expensive compared to those that are software-based. Due to budget issues, they are more recommended for bigger businesses and corporations.
Manually Creating VPN Configuration
If manually creating a VPN configuration is an option for you, the steps on how to do so are not really tricky to follow. In fact, the User Office provides you with different ways in which you can manage your account. In fact, you can even create files for VPN configuration on your own.
Choose a Device
Choose a device from the list under manual configurations, or create a new one. If you notice that there are no free slots available, you can delete a previous device or purchase extra slots.
Select the Ideal Server Location
One provider, the KeepSolid VPN Unlimited, can be used as it features a wide range of servers, with up to 400 or over of them across 80 or more locations.
Choose the VPN Protocol
Under the IKEv2 protocol, there is a need to specify the platform of your device.
Create a VPN Configuration
As you press ‘Generate’, you can get all of the data that you need in order to get a VPN connection. This data often includes login, password, as well as server address, among others. They will be available in the form of QR code and text. A configuration file will also be downloaded when using IKEv2 on Windows.
Conclusion
With the need for VPN continuously increasing, individuals and corporations are now focusing their attention on VPN configurations with the goal of protecting any sensitive data and information that they may have. A number of reliable options are currently available these days, which is why choosing the best one is homework for everybody. Note, however, that there are also some limitations to a Virtual Private Network. For one, there is a risk of introducing malware to the network environment. For this reason, certain precautionary measures need to be addressed eagerly.