Malware is a nefarious operating system that can smuggle into your mobile device. Malware may include viruses, computer worms, Trojans, ransomware, and spyware. Malicious hackers might use malware to manipulate your private information and, in some situations, use confidential information to facilitate fraud or other crimes.
Viruses are a specific form of malware that infiltrates a desktop or even other device and their applications. People may indeed be required to activate a virus on their device without your permission or knowledge. The virus may also be able to incorporate the latest malicious content into your gadget that can control and exploit your internet behavior.
Some tips and trivia that you need to know on how to remove malware from android
Let us be honest about everything, and there’s something like Android malware, malicious hackers are creating malicious programs to steal private information, exhibit unusual behaviors, or reroute the victims to a fraudulent web. Mobile devices engineered to customize people’s Android-based mobile devices, and some recreation and game development software is most likely to be exploited.
The large percentage of Android malware is based on manipulating your identification, including such credit card data, phone contacts, or other personally identifiable information. That being said, there has been plenty of malicious software that show intrusive ads on the phone or inside the website and lead victims to the fraudulent web.
Computer hackers get a legal android software package file and connect it to exploit android devices with malicious software. Many pirated or modified applications typically have some sort of malware, so we persuade you never to download these applications.
Step by step procedure on how to remove malware from android:
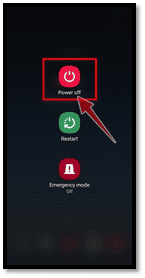
1. Long press the button for power off
Click the software power switch (positioned just at sides of your mobile device) for a long time before the shut-off screen appears.
Now that you are sure that malware attacks, you’re mobile, keep the power button, and switch off the mobile device entirely. It may not stop malware from causing harm, but it may impede the concern from growing more durable and may prevent existing tries to penetrate surrounding channels.
Trying to shut off also gives you plenty of time for reading and analysis. Unless you can’t seem to find the bug at the root of the problem, you can’t take it away.
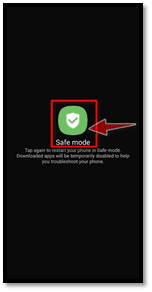
2. Click on the “Safe Mode”
Click it to access secure mode whenever the “Safe mode” choice occurs on your display. Swap first to secure feature, when turning your phone back on and plunging in to detach the troublesome app. It will also help to curb the destruction that the diseased software can really do.
When your computer is switched on too many mobile devices, you could toggle to standby mode by pressing press the power key for a few seconds, then pressing and keeping the power off button. This will drag up some power options, as well as the Reset to Safe Mode method.
Chose this particular mode and allowed time to restart your mobile device before proceeding. If you can’t seem to find a control center, conversely turn on the flight mode to cut apart your gadget from any channels.
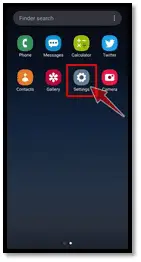
3. Delete suspicious software from your mobile device
Applications use the system access to execute reasonable duties such as system configuration or a distant location flush for antivirus software. Regrettably, malicious software also uses those administrative privileges to help prevent victims from discarding the mobile device’s malicious program. Throughout this second phase, we’ll search the machine to see whether there are any suspicious apps mounted on your device with system privileges.
Access Your Android App Settings. Configurations usually have such an equipment-shaped icon, but that varies depending on your concepts and configuration: when you have problems remembering spot, look for it.
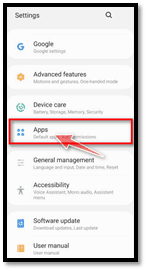
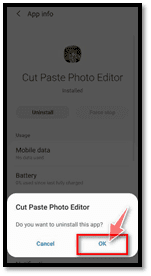

4. Remove and delete suspicious applications on your android device
Inspect to see if your mobile device has any malicious software configured. Often client hijackers or virus protection apps might have functional Disable entries for removing such items. Toggle the “Setup” button on your settings page or phone menu. When another menu “Settings” unlocks, press “Tools” to see all of the programs installed on your computer.
The “Apps” screen will appear with a catalog of all the software downloaded on your mobile device. Measure the number before you find the hostile app. Watch out for some odd update software that you don’t recall and that it doesn’t seem like a legitimate application. Computer hackers frequently conceal malware within video or encoding devices, weather devices, or even in the camera apps.

5. Install or Download antivirus/malware application on your phone
Almost any smartphone deserves and requires protection, especially one which is highly susceptible. You can install a wide range of security tools that can help secure your computer, search for malware, and get away from malicious software and other potentially exposed devices. Once you complete removing the problematic device manually, install antivirus software to assist with any potential issues. There are several options in this domain: Check out Google Play Store apps such as Secure Protection, Avast Antivirus, or Advantage Antivirus, and others.
Other things that you need to remember and take into consideration on how to remove malware from android:
To guarantee the protection program, you spend in operating a full scan and do not ignore any bugs, and it’s a smart strategy to do your homework. An incompetent scan may give you a lacking and wrong sense of privacy and security when your mobile devices might actually be susceptible to cyber and malfunctions attacks. It is a smart option not to delay before you get contaminated with your computer. Give more attention to safeguarding your android operating system. Maintaining a decent antivirus system that allows help to defend your PCs, tablet computers, and some other mobile devices might hopefully minimize malware from spreading from location to location. Mobile devices can be susceptible to external and underlying destruction. Although the exterior removal tends to be noticeable, the inner condition is usually completely hidden.



