The term Malware is short for malicious software. It is the term used for any type of program designed to harm or exploit any device or network. Malware consists of codes that are put together by a team of cyberhackers with the intention of wreaking destruction, gaining unauthorized access, steal sensitive personal information, or selling it to the highest bidder.
Brief History of Malware
Malware has been a threat to many organizations and individuals since the dawn of computing itself. The earliest documented virus, however, was in the early 1970s when the “Creeper worm” first appeared. It was an experimental self-replicating computer program created by Bob Thomas to illustrate that computer viruses are possible. Since then, thousands of different malware variants have been created. But while the Creeper worm only displayed its enigmatic message “I’m the creeper, catch me if you can!”, the viruses that we continue to deal with today are intended to cause destruction.
How Malware works
Malware authors create their programs to do a number of different things. From encrypting files to demanding ransoms to destroying data to stealing sensitive personal information, how malware works is a pretty broad category. Unfortunately, there is a lot of malware out there, but here are some of the most common types of malware:
Viruses
A virus is possibly the most common type of malware as they act like their biological namesakes and spread rather quickly. These types of malware usually come as an attachment in an email, usually as an executable file (.exe), that holds a malicious code. Once the victim opens the file, the virus payload inserts itself to the clean codes, causing extensive damage to the core functionality of the entire system.
Worms
As their name implies, worms can reproduce themselves from machine to machine. It’s the ability to weave their way through networks autonomously, without any human interaction or the need to hijack the codes on a software program, that distinguishes the worms from other types of malware. They cause damage similar to viruses – exploiting loopholes in system security, stealing sensitive data, and corrupting files, among many others.
Spyware
This class of malware is aptly named because it is designed to secretly observe and work as a spy. It is installed on a computing device with the aim of gathering private information about an organization or a person, without their knowledge, and relaying this information to snooping external users, data firms, and advertisers.
Ransomware
This type of malware can lockdown an individual or organization’s entire computer system, and networks threaten to erase everything or publish the data unless a ransom is paid. Depending on the type of attack, ransomware removal can vary from very simple to very advanced. A simple ransomware will not be difficult to reverse and unlock. However, much-advanced ransomware, called cryptoviral extortion, comes with a very heavy price and is usually targeted at some of the biggest organizations in the world today.
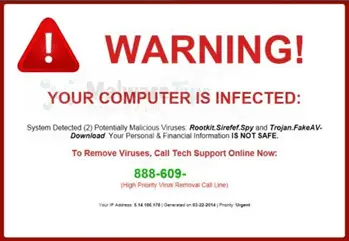
Scareware
This malware tactic scares users into thinking that their devices are under attack, and they need to download a fake application, like fake anti-virus software. You might see an alarming pop-up that says, “Warning! Your computer is infected!” Once the user downloads the advertised or suggested application, this will be used to steal personal data and banking information. Scareware is also known to attempt to remotely control computers to use them as part of a spam-sending botnet.
Bots
Bots can be used for either good or malicious intent. However, for the past decade, malicious bots are fast becoming one of the most popular methods of malware deployment. A malicious bot is a self-propagating malware that has the capability of infecting a huge number of computers. They leave an extremely small footprint but have the amazing ability to log keystrokes, gather personal data and financial information, open backdoors, and, ultimately, connect all of these back to a central server. The server acts as a command center for the entire network of compromised devices, now referred to as a “botnet.” Many unsuspecting owners of infected computers are probably not aware that their system has been infiltrated as they can still use their devices.
Trojans
Named after the wooden horse that the ancient Greeks used to infiltrate Troy, this type of malware also masquerades as a harmless, legitimate application in order to enter a system. Once inside, it can achieve a number of attacks against the host computer. It can sit quietly in your computer, collecting sensitive information, or it can opt to launch an attack over your computer and lock you out. Trojans are also known to breach security to work as a decoy horse to create a backdoor and usher in other malicious software into the system.
Adware
Though not always malicious in nature, adware programs generate revenues for their authors by pushing an onslaught of unwanted and insistent advertisements at users. They often come as annoying pop-ups or slide-ins when you try to perform a certain action. And sometimes, they might even redirect you to new tabs selling dubious products. Once this type of malware hijacks your system, the program analyzes your behavior in order to present you with more pesky advertising. To simply serve you these advertisements, the aggressive nature of adware programs can undermine the system’s security and can give other malicious software an easy way in.
Malvertising
Not to be confused with adware, malvertising is another form of cyber attack that perpetrators use to distribute malware through legitimate online advertising networks. Online advertising, which involves ad exchanges and retargeting networks, is a vital part of many websites and malvertising takes advantage of this complex ecosystem. It places malicious codes in places that online vendors and ad networks would lead expect. The end goal of “malvertisers” is to trick unsuspecting individuals to download malware or direct them to a malicious server.
How to protect against malware
Now that we have understood some of the many types of malware applications and how they work, it is easy to see that we need to know how to protect ourselves from these malicious programs. As they say, prevention is always better than cure.
Protective tools
- Ensure your device’s operating system and applications are updated. Cyberattackers usually look for loopholes and vulnerabilities in old, outdated systems to launch their attacks.
- Install an anti-virus protective software that can manage and update itself. Despite “virus” being in the name, these programs are known to take on all forms of malware.
- Get an ad blocker that you trust. Since it is quite difficult to know which advertisements are bad, these programs are designed to alert you on the first sign of adware or malvertising.
User Vigilance
- From phishing emails to official store sites, malware could just be lurking around the corner. The best way to protect yourself from these malicious programs is to educate yourself with the common scams and double-check that the provider is trustworthy before double-clicking on anything. If you are not sure what it is, do not click it.
- If you are concerned that your device is running slow and may be infected, run a scan immediately.
The alarming rise of malware attacks over the past years should be a cause for concern for everyone. Education is the first step to ensure that we are aware of the risks of these programs and what damage they can do. The reality is that malware developers continue to develop a number of sophisticated strains of malware to launch their attacks. Taking actions to stop and prevent these malicious programs should be a top priority if we want to keep our online activities safe and secure.



